Intune has been using a RBAC model since a while now. Let’s have a deeper look at ‘Scope Tags’. What can we do with this, what is it used for and what are the limitations.
Scope Tags can be used for distributed IT Teams to ensure that the configuration gets only applied to devices and users they are responsible for.
An Admin can then only see / change / save items within his scope tag. He can also only make assignments to user and device groups within his scope
Setup
Let’s start with the following scenario:
We will have three different locations and we want to separate them from an administrative perspective.
- Frankfurt
- Nuremberg
- Munich
We will have three groups per location
- Devices: all devices related to the location
- Users: all users related to this location
- Admins: all admins related to this location
Configuration
Create Scope Tag
First of all, we have to create one or more scope tag. Go to Intune → Roles → Scope Tags. There you can create custom Scope Tags.
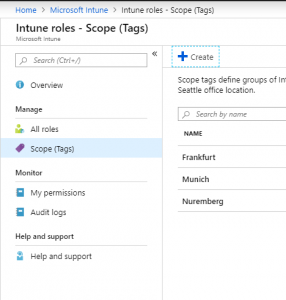
Use Roles
What is a role? Roles are a bunch of settings to allow administrators very specific tasks to do in Intune. A role has two sections. Permissions and Assignments
Within the permissions you can – how obviously – define which permissions you want to delegate
Within the Assignment you’ll have three sections:
- Members: Who will get the new permission
- Scope (Groups): Which groups should be managed. This can be a device and/or user group
- Scope (Tags): Which tag will apply.
You can have multiple assignments in one Role. But let’s keep it simple and use only one assignment
Let’s create a new Role. Go to Intune → Roles → All Roles and add a new role
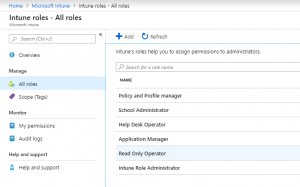
You will first have to define what permissions you want to delegate to them. Please select all your required permissions and click create. If you want to can also Scope that role. Don’t let the wizard upset you. This scope is not relevant for the delegated admin at this point.
Now it’s getting interesting. Go into your new role, and create a new assignment.
- Members, please use a group where your admins are in who want to delegate permission to.
- Scope (Group): This is a list of target groups where your delegated admin can have permissions to.
- Scope (Tags): A list of Tags this assignment is relevant to
How does it look like
Now we want to see how it look like for admin Admin which has permission to Franfurt related stuff.
You’ll see, admin global admin can see all policies in this case. An admin which is limited to the scope ‘frankfurt’ can only see policies with no tag and policies with his tag(s), but not policies with other tags.
If an admin with scope tags create new items, they’ll automatically inherit his all of his scope tags.
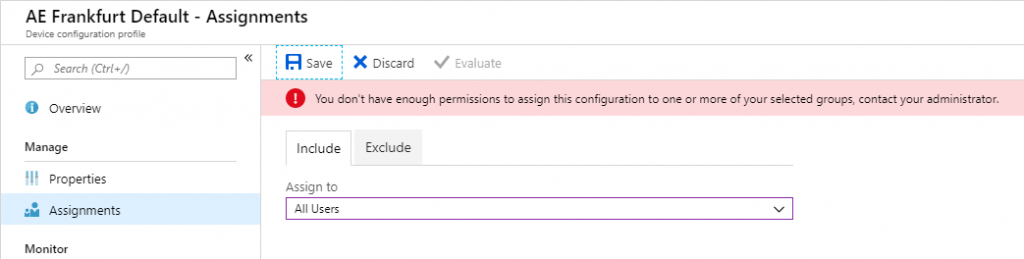
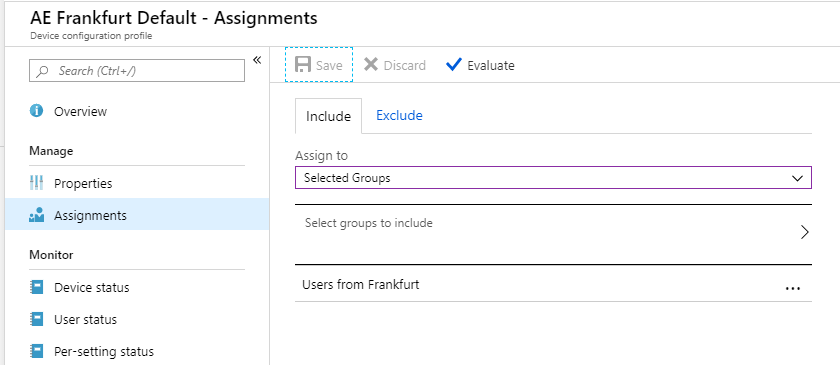
An admin can only target groups listed in his scope (group) assignment. This is how it look like if an admin try to assign a policy to all users vs. to his users groups
Lessions learned
- Admins with scope tags can see policies with NO scope tag and policies with scope tags assigned to him
- Newly created items always inherit all of his scope tags
- Change items with no scope tag will then require a scope tag
- Admins can only target groups that are listed in the scope (Group) of his assignment
- New created or changed items by an admin need at least one scope tag
Please let me know if you have any concerns or any other feedback to this guide
stay tuned
Simon

Came across this and really helped understand the use of scope tags. thank you, much appreciated.
Thank you for your kind reply. Glad to help you.
I think this is what I’m looking for but not sure
We are one of 20 schools but we all come under one office 365 tennant
We want each schools admin to see and administer devices in there school
Do we use scopes and tags